Bypassing Carbon Black Defense + Protection + Response
In this post, I am going to demonstrate a new bypass on the Carbon Black solutions with the maximum security enforcement and configuration as well as all the Threat Intelligence feeds are enabled in the CB Response.
Environment Settings
Running Products:
- Carbon Black Protection – (Application control)
- Carbon Black Defense – (NGAV)
- Carbon Black Response – (Endpoint Detection and Response)
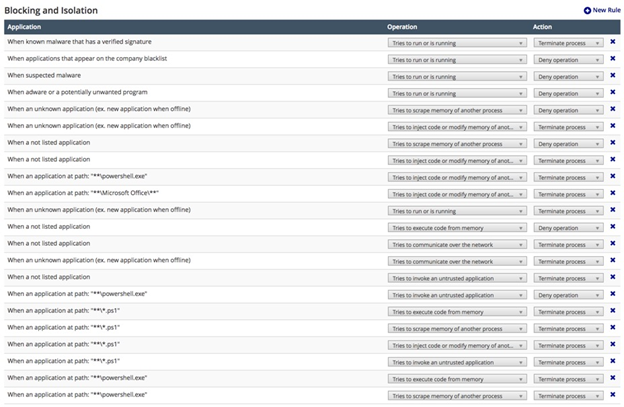
Carbon Black Defense:
I am using the most restrictive and harden profile that I customised for this attack.
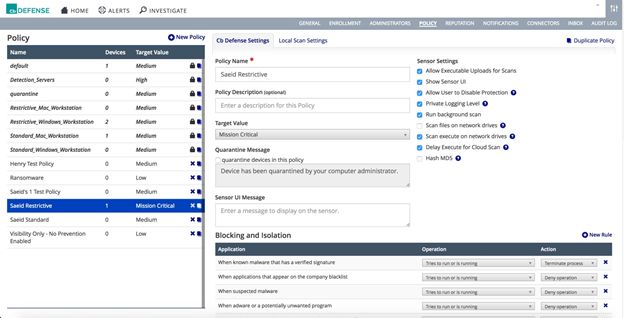
And the rules are as listed as below.
Carbon Black Protection:
Application whitelisting is enabled, and it is at the maximum-security mode, that means, unknown files won't be able to run at all.
Carbon Black Response:
There isn't profile setting on the Carbon Black Response except the I can enable all the IOC feeds which I did.
The target machine CB version: 2.0.3.4
The Attack
There are multiple ways to get into victim systems, one of the popular methods is WPAD/HTTP man in the middle attack which I have used to get the NetNTLMv2 hash and then recovered the password from it.
Next, after cracking the password, one of the common methods would be to use psexec to execute commands and getting a reverse shell.
But we never received a shell as CB has blocked it. Let’s have a look at the CB Defense logs.
As it’s been visible from the above screenshot, the CB Defense blocked my attack because the powershell.exe attempted to load the library.
By rechecking the CB rules, there are restrictions configured for “powershell.exe” and the process is not able to make some specified actions.
Since I already gave up on using psexec to achieve my goal and get a successful reverse shell, I also tried to make a bind shell working, but unfortunately that didn’t work too.
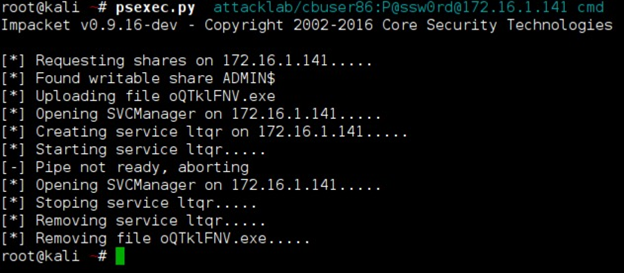
The following is the CB logs right after executing a bind shell.
Last try: I used Microsoft signed Psexec.exe tool to do the same. And unbelievably it worked!
Finally…
Since I could successfully establish interactive access to the victim with the legitimate PSEXEC.exe from Sysinternals Suite, I tried to use other methods such as PowerShell onliners to execute a payload through the psexec, but those all failed.
Logs are shown below:
I also tried different ways to execute shellcode on the target machine such as Cscirpt and regsvc32, but unfortunately, all failed again.
By looking into the CB Defense rules one more time, I noticed that CB Defense is hardcoded the powershell.exe and its blocking the "powershell.exe" with a wildcard prefix!

Last try:
I used Sysinternals psexec.exe which is digitally signed by Microsoft, to copy the user’s PowerShell from his machine to his temp folder, rename it and then execute a beacon PowerShell oneliner through that already renamed “powershell.exe”
The following shows the same..
I copied the powershell.exe to temp folder with the name of x.exe and executing x.exe
Successfully established a reverse shell through all the Carbon Black products installed.
Since we got system, we can safely invoke mimikatz and other stuff without getting detected.